Malware Intrusion and Loss of Company Assets & Data
Malicious or criminal attack
is highest reason
Major Causes of Data Breach


48%
Data Leak Damage
(in 100 million dollars)
2018
Leakage
Cost
38.00
Follow-up
Processing Cost
25.00
Source : Ponemon 2018 Cost of a Data Breach Study
Malware Intrusion and Data Leak
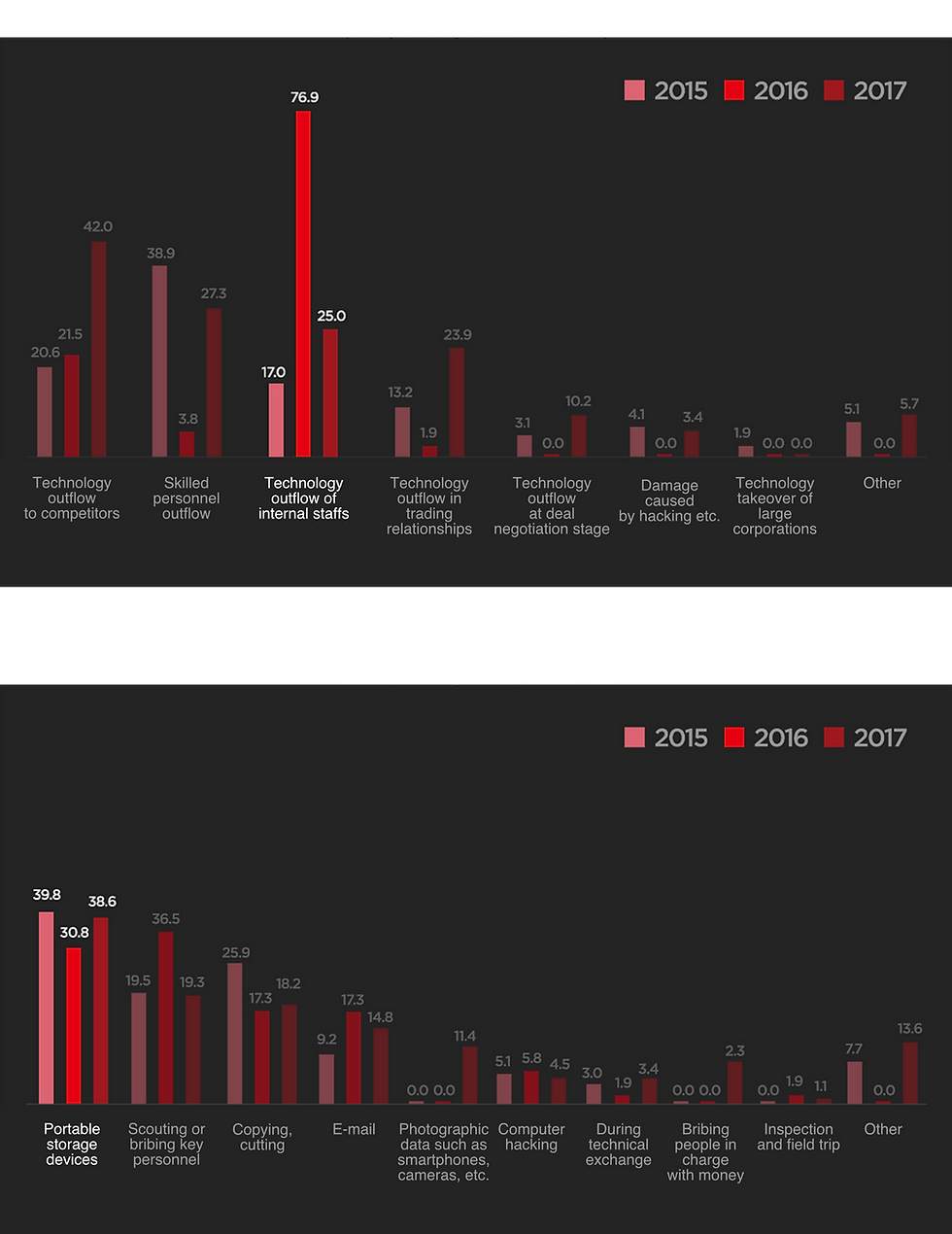
Types and Means of Technology Leakage
.png)
Major Cause of Industrial System Malware
Removable data storage is
still a major threat to security

Malware Intrusion and Data Leak
How many people would plug in a USB drive that tehy picked up on the street?
USB drive picked up on the street is used by an employee on an in-house PC

In 2011, the US Department of Homeland Security US-CERT (United States Computer Emergency Readiness Team) conducted an experiment on security staff. ‘How easily hackers can access the system through employees’. The experiment was to drop a USB drive into the parking lot of the security department and see if the employees were using it on the in-house PC. What was the result? About 60% of them used a USB drive which fell to the ground, and 90% used a USB drive or CD with official logo of DHS. “I forgot all the risks that there might be malware in the USB and used it on my PC.” The biggest security vulnerability is the employee’s “idiocy”.
Malware Intrusion and Data Leak
A Single Malware Infection
Can Cause Catastrophic Damage

Two US power plants infected
with malware spread via USB drive
Two US power plant networks were infected with malware that was spread by a USB drive plugged in by a subcontractor, who wanted to check on production facilities.
The malware affected 10 PCs in the turbine management system and system downtime, which caused a 3-week delay in system restart. Supervisory Control and Data Acquisition (SCADA) or Industrial Control System (ICS), that is, industrial control systems are especially vulnerable to immediate threats of machine interruption or remote attack. Malware infection path was a USB port this time, but all other open data ports were equally vulnerable.
Malware Intrusion and Data Leak
One Small Act of Thoughtlessness
Under worm assault, military bans disks, USB drives
An example of a cyber attack designed to destroy nuclear centrifuges is the Stuxnet worm attack, which infected the Supervisory Control and Data Acquisition (SCADA) system at Iran’s Bushehr nuclear power plant. Through a USB drive, malicious codes spread throughout the internal network, infecting more than 60,000 PCs and halting the plant’s operation for two years.
Many companies, including power plants, the military and others, have already taken measures to prohibit the use of removable data storage devices such as DISK and CDs for increased cyber security.

Do you know the USB KILLER?
More popular and closer attack methods
This easily accessible product is designed to rapidly collect current from the USB power source. Once fully charged, it releases the high voltage and burns all of the circuits, effectively “killing” the computer.
In one case, the owner of a local PC Cafe intentionally damaged approximately 40 PCs of a competitor using the USB Killer.

Recently, in April 2019, a college student in the U.S. used a USB Killer on his school system, causing $58,000 in damage.

Physical Cyber Security,
Now a must, not a choice.
There will be more and more cases similar to these,
and the damage to companies will increase.
Do you still think cyber security is just about software?